SSO: OIDC with Okta
This guide walks you through the steps to configure Single Sign-on using OIDC with Okta.
Prerequisites
Before you begin, ensure you have admin access to your Okta dashboard.
Step 1: Set Up an Okta Application for Control D
Note: If you intend to use specific controld-* groups (e.g., controld-admin, controld-owner, controld-viewer) for role-based access, create these groups first as outlined in Step 4.
-
Log in to your Okta Admin Dashboard.
-
Navigate to Applications and click Create App Integration.
-
Select OIDC - OpenID Connect as the sign-in method and choose Web Application as the application type. Click Next.
-
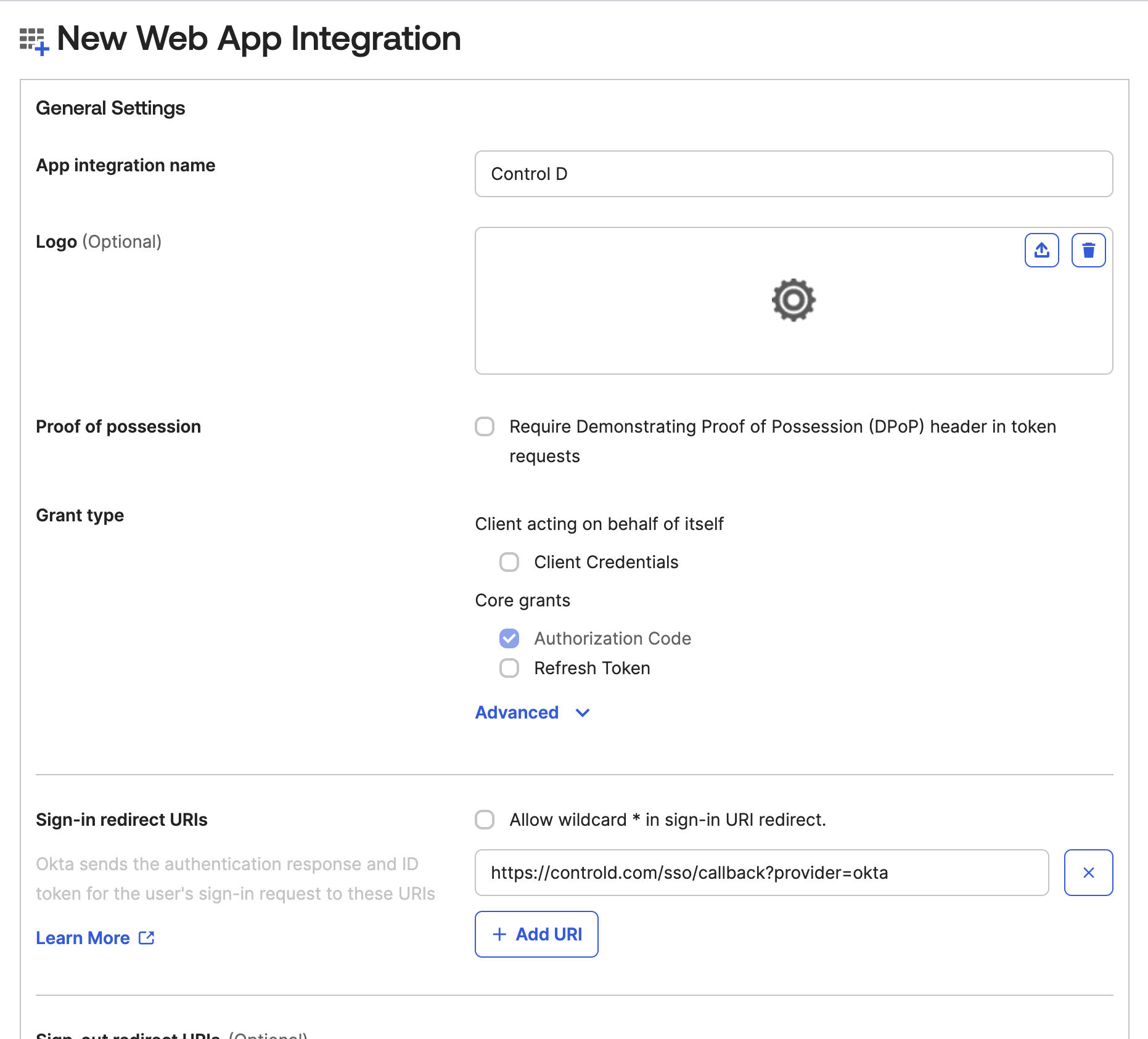
Fill in the application details:
Field Data App Integration Name Control D Logo (Optional) 
Sign-in redirect URIs https://controld.com/sso/callback?provider=oktaSign-out redirect URIs Delete all entries
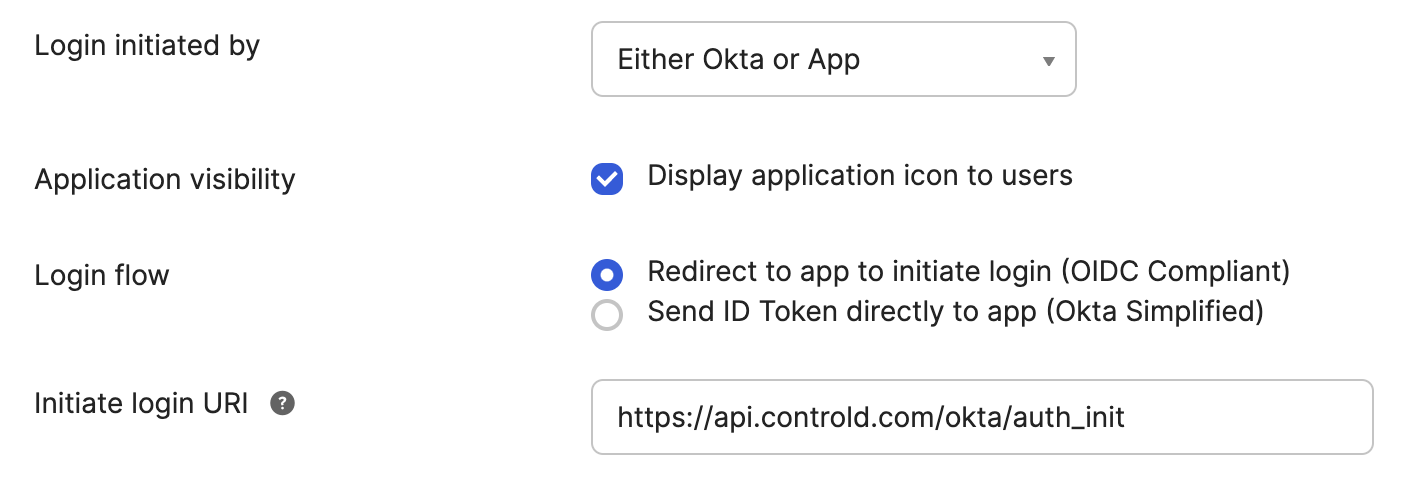
For IDP Initiated Login supportThis allows for one-click login from the Okta user homepage
Field Data Login initiated by Either Okta or App Application visibility Display application icon to users Login flow Redirect to app to initiate login (OIDC Compliant) Initiate login URI https://api.controld.com/okta/auth_init
- Under Assignments, you can assign people or groups to the application, or select Skip group assignment for now if you wish to assign them later.
If you plan to use role-based groups, assign thecontrold-*groups (controld-admin,controld-owner,controld-viewer) created earlier.
ControlD.*andcontrold-*are both supported group formats.
- Ensure the Grant Type is set to Authorization Code.
- Click Save to create the application.
Step 2: Configure the Okta Application for Control D
-
Open the newly created Control D application in Okta.
-
Go to the General Settings tab and note down the Client ID and Client Secret.
-
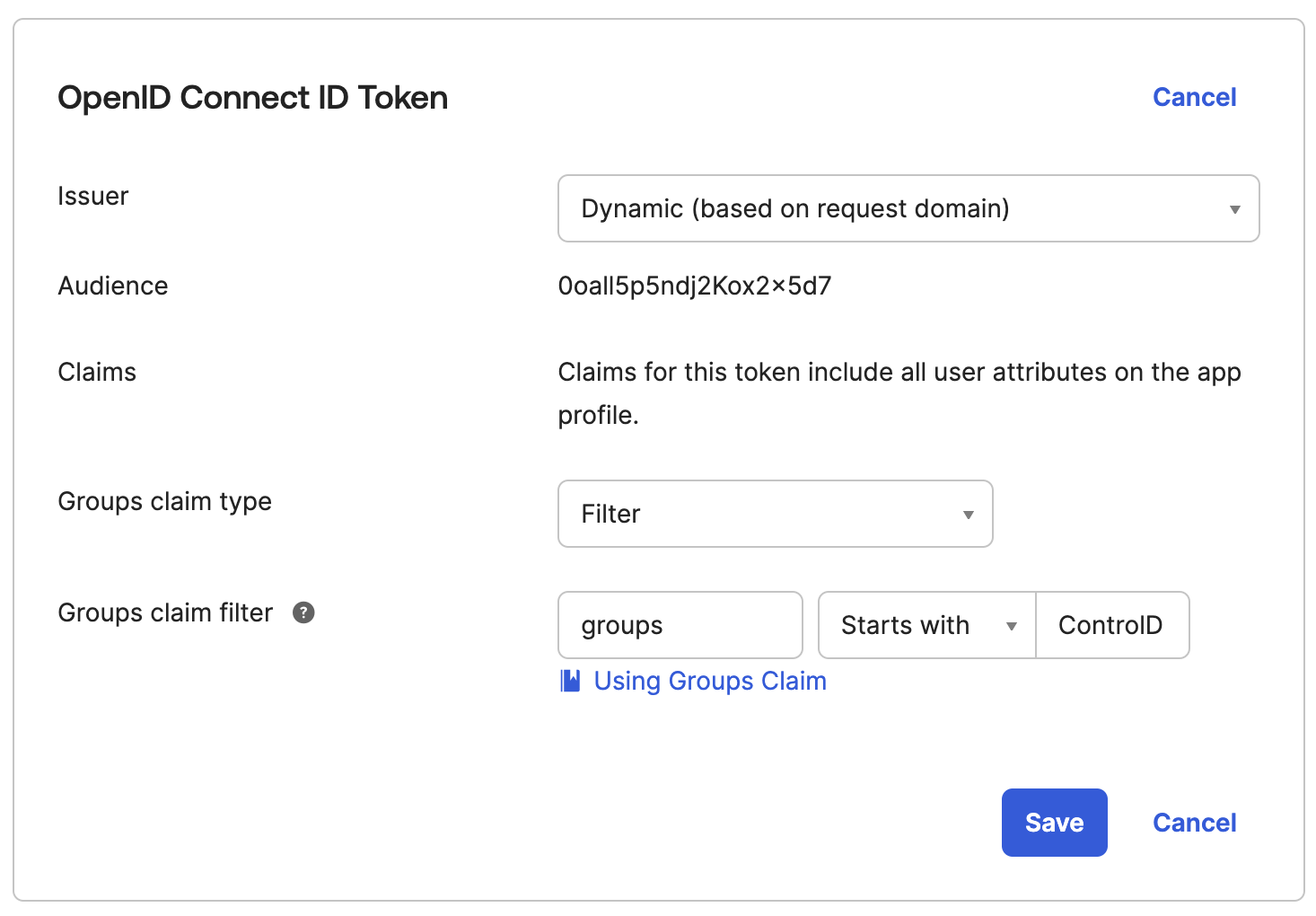
Go to the Sign On tab and ensure the OpenID Connect ID Token option is enabled.
-
Under Groups Claim, set Groups claim type to Filter and choose Starts With. Enter
controldto include groups such ascontrold-admin,controld-owner, andcontrold-viewer.
Step 3: Assign User Groups in Okta
A feature to support custom group mappings is under way!
Note: If you have already created the controld-* groups, you can skip creating new groups and proceed to assign users to the appropriate permissions.
-
Go to Directory > Groups in Okta.
-
Create three groups for Control D access (if not already created):
controld-admincontrold-ownercontrold-viewer
-
Assign users to these groups based on their roles and responsibilities within Control D.
Learn about the different roles and permission levels here: https://docs.controld.com/docs/org-members-permissions#permission-levels
Step 4: Add SSO Configuration in Control D
-
Log in to the Control D.
-
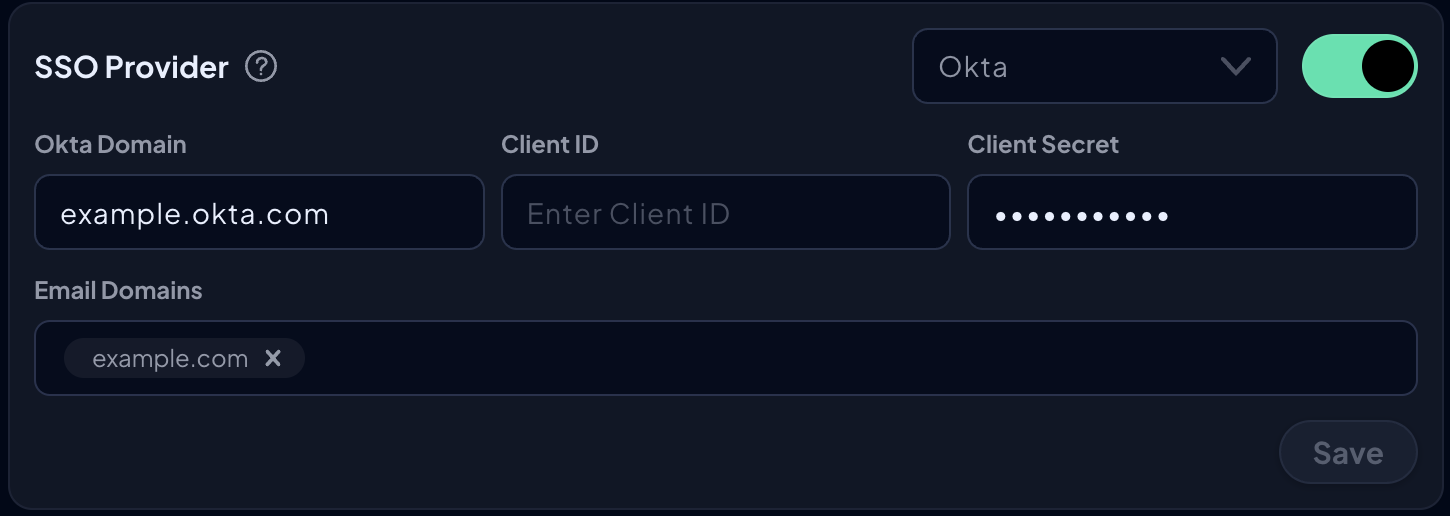
Navigate to My Organization, scroll to SSO Provider, and click the toggle to enable.
-
Fill in the required fields:
- Okta Domain:
<your-subdomain>.okta.com - Client ID: The value you copied from the Okta application.
- Client Secret: The value you copied from the Okta application.
- Email Domains: Enter the domains associated with your organization, e.g.,
example.com. This is necessary to map email domains to your Control D customer account so that login attempts are redirected to the correct Okta authentication server.
- Okta Domain:
-
Click Save to enable Okta SSO for your organization.
Step 5: Test SSO Login
- Log out of Control D and navigate to the login page.
- Enter your Okta email address, leaving the password blank.
- Click the Log in with Okta button.
- Enter your Okta credentials and confirm successful login.
- Verify role-based access permissions by testing users in the
controld-admin,controld-owner, andcontrold-viewergroups.
Troubleshooting
If you encounter any issues:
- Verify the redirect URIs in your Okta application settings.
- Ensure the user groups are correctly assigned in Okta.
- Check the SSO configuration in the Control D Admin Panel for typos or missing fields.
- Refer to the Okta logs for debugging SSO errors.
For additional support, contact Control D Support.
Updated 4 months ago